Runtime firewallfor
Detect and block unexpected outbound connections from dependencies, MCPs, and AI-generated code at runtime.
How it works
From install to protection in minutes
Install Jibril—our lightweight runtime agent—to monitor code behavior at runtime. From CI builds to Kubernetes deployments, automatically block malicious activity and get alerts in your existing workflows.
Protect your build, staging, and production workloads with one lightweight agent. Install via Helm for Kubernetes clusters or as an Action for CI/CD runners.
v2.8
staging
build
production
Detect live attack behaviors like C2 connections, exfiltration, backdoors—surfaced with kernel-level visibility, lineage, and source context.
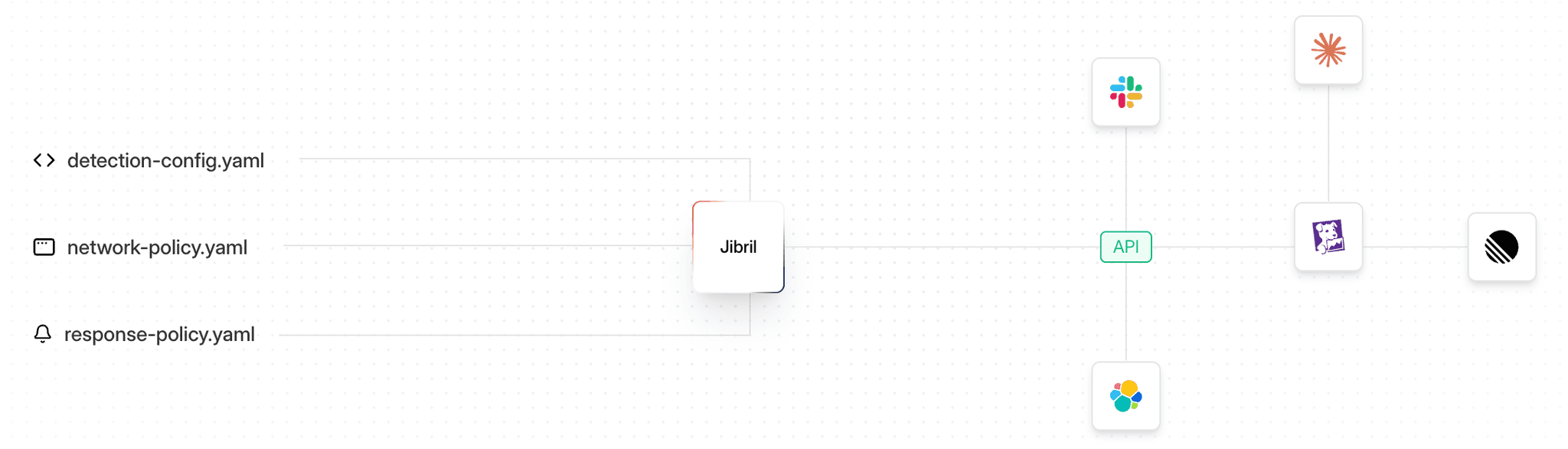
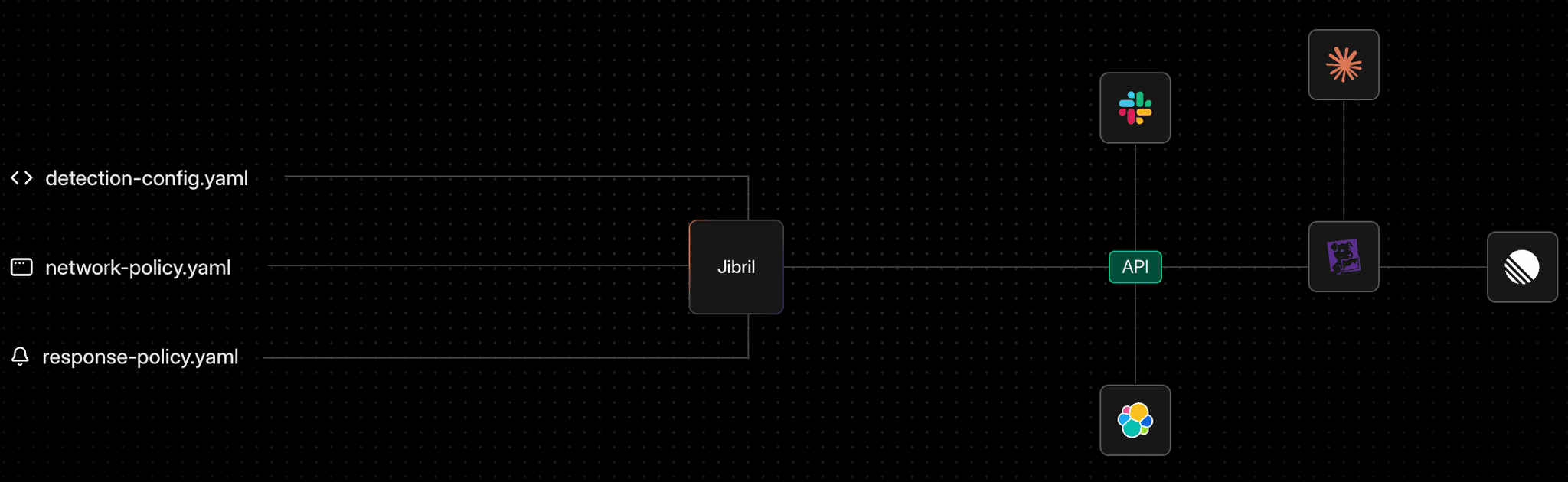
Get in-line feedback directly in Slack, GitHub, or any tool you already use. Every alert includes rich runtime context so teams can triage and respond faster.
Behavioral runtime monitoring
for code execution
Garnet sees what code actually does as it runs. Flag anomalous behaviors that signal compromise or supply-chain attacks in real time, not after the fact
Lightweight runtime agent
Deploy a high-performance eBPF agent in a few clicks, providing deep runtime visibility across any workload where code executes.
v2.8
Managed detections, out of the box
From malicious network traffic to file tampering and reverse shells, you get continuously updated detections built from our in-house threat intelligence.
In-kernel behavioral detection & response
High-fidelity runtime behaviors enriched with MITRE ATT&CK context. Stream behavioral insights directly into your workflows through our rich API integrations.
Minimal overhead, massive scale
Lightweight eBPF agent runs with low overhead. Protect workloads at scale without performance trade-offs.
Policies with behavioral context
Every runtime policy is enriched with deep behavioral context to eliminate noise. Clear, actionable insights your team can trust.
Stop threats instantly
Block malicious activity at the kernel before it spreads. Terminate cryptominers, access to C2 servers, and more in real time.
Use Cases
Protection against supply chain attacks
Stop malicious system behaviors and actions triggered by compromised code running in your workloads—from build to production.
Remote code execution (RCE)
Stop unauthorized code execution (shells, injected processes, or malicious binaries) in your workloads and prevent attacker control.
Backdoors
Detect and terminate reverse shells, bind shells, and persistent implants used to establish unauthorized interactive access.
Cryptomining
Terminate unauthorized cryptominer processes and block connections to mining pools in real time.
Command & Control (C2) traffic
Prevent DNS and IP communication with attacker-controlled servers before persistence is established.
Data exfiltration
Monitor and block unauthorized transfers of secrets, credentials, or sensitive data to external destinations.
Vulnerability exploits
Identify and stop runtime exploitation of known and zero-day vulnerabilities before they spread laterally.
Trusted by leading teams

"There are a lot of tools that process security advisory data, but Garnet is the first I've seen that goes a step further, applying behavioral analysis to find issues before they get reported to an advisory database. This is the kind of thing we'd always wanted to do at npm, Inc., but never got around to. It's super exciting to see it come to fruition."

Isaac Z. Schlueter
Creator of NPM, cofounder, Volt.sh
Benefits
Why engineering teams choose Garnet
Deep runtime visibility. Low overhead. Instant integration. Garnet fits into how your team already works.
Deploy in minutes
Instant visibility into code behavior at runtime with a single Helm install or GitHub Action. No code changes required.
Insights that matter
Behavioral policy detections cut through the noise, surfacing only meaningful insights tied to suspicious code execution or system activity.
Scale without overhead
Lightweight eBPF agent scales across clusters and runners with very low overhead, designed for production-grade workloads.
Egress Detections
test-runner • Last 24h
Real-time protection
Block or flag malicious system behaviors in real time before compromised code can spread.
Runtime coverage
Full observability across the SDLC, with an audit trail for compliance and investigations.
Deploy and forget
Once installed, Garnet monitors in the background 24/7, analyzing system activity at runtime and only alerting when it detects suspicious or compromised code behavior.